
In today’s world, keeping our digital lives secure is crucial. Ethical hacking helps protect against online threats, and hands-on projects are a great way for beginners to learn.
This article offers over 35+ ethical hacking project ideas for beginners in 2024. These projects will help you take what you’ve learned and apply it in real-life situations. Whether you’re new to ethical hacking or want to improve your skills, these ideas will guide you as you get started and build your knowledge.
Check out these easy-to-follow projects designed to help you learn and practice ethical hacking.
Survey Results: Challenges in Choosing the Right Project Idea
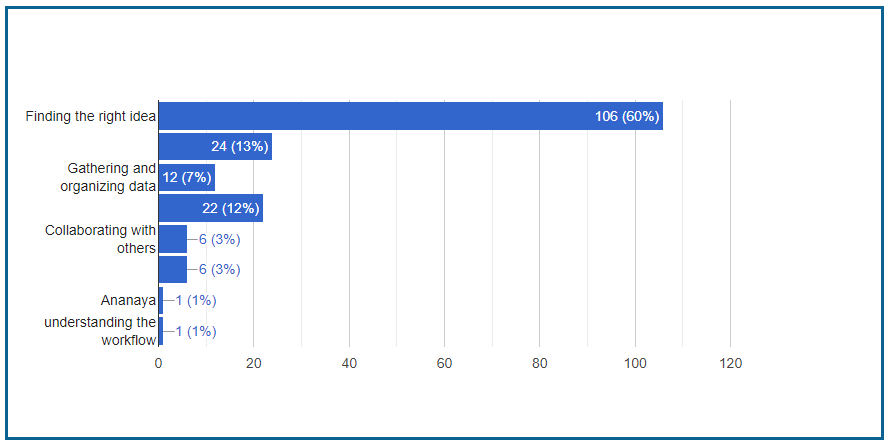
We recently polled 178 people and found that many struggled to identify the best project idea. The majority of participants said they required help choosing a project.
What is Ethical Hacking?
Ethical hacking, also called white-hat hacking, is when someone tests the security of computer systems, networks, or apps to find and fix problems before bad hackers can use them. Ethical hackers help protect systems by spotting and correcting weaknesses.
How Ethical Hacking Works
- Planning: Ethical hackers start by learning about the system and deciding what to test.
- Scanning: They use tools to look for security issues.
- Exploitation: They try to exploit these issues to see how an attacker might break in.
- Reporting: They write down what they found and suggest how to improve security.
Why Ethical Hacking is Important
- Finding Weak Spots: Ethical hacking helps find and fix security gaps before bad hackers can exploit them, preventing data breaches and cyberattacks.
- Improving Security: Regular testing keeps security measures up-to-date and effective against new threats.
- Meeting Rules: Many industries have strict data protection rules. Ethical hacking helps organizations follow these rules by finding and fixing security issues.
- Building Trust: By fixing security problems, organizations show they are serious about protecting information, which builds trust with customers and partners.
- Preparing for Real Attacks: Ethical hackers simulate real attacks to help organizations see how they would handle actual threats, making their response better.
In short, ethical hacking is crucial for keeping digital systems safe. It helps find and fix security issues, ensures compliance with rules, builds trust, and prepares organizations for real threats.
35+ Essential Ethical Hacking Project ideas for Beginners to Master in 2024
Here is the list of 35+ Essential Ethical Hacking Projects for Beginners to Master in 2024
1. Port Scanner
Objective: Create a tool to scan a network and identify open ports on a target system.
Description: A port scanner detects open ports on a system, revealing services running on those ports. This helps in assessing network security and identifying potential entry points.
Tools: Python, Nmap, Netcat.
2. Password Strength Checker
Objective: Develop a tool to evaluate the strength of passwords and provide suggestions for improvement.
Description: This tool assesses passwords based on criteria like length, character variety, and common patterns, helping users create stronger passwords and enhance security.
Tools: Python, Regex.
3. Network Sniffer
Objective: Build a basic network sniffer to capture and analyze network traffic.
Description: A network sniffer captures packets traveling across a network. Analyzing these packets helps understand traffic patterns and identify potential security issues.
Tools: Wireshark, Scapy.
4. Simple Keylogger
Objective: Design a keylogger to capture keystrokes and understand its methods of detection and prevention.
Description: A keylogger records keystrokes typed on a keyboard. It is crucial to use this tool ethically and only in controlled environments for educational purposes to understand its functioning and protective measures.
Tools: Python, PyHook, Pynput.
5. Vulnerability Scanner
Objective: Develop a basic scanner that looks for common vulnerabilities in software or web applications.
Description: This scanner checks applications or systems for known vulnerabilities, such as outdated software or insecure configurations, helping to identify and address security weaknesses.
Tools: Python, Nmap, OpenVAS.
6. Ping Sweeper
Objective: Create a tool that pings multiple IP addresses to determine which are active.
Description: A ping sweeper helps map out active devices on a network by sending ping requests to a range of IP addresses, aiding in network management and security assessments.
Tools: Python, Ping.
7. Basic SQL Injection Tester
Objective: Build a tool that tests web forms for SQL injection vulnerabilities.
Description: SQL injection involves inserting malicious SQL code into input fields. This tool tests web forms with SQL injection payloads to find vulnerabilities and improve web application security.
Tools: Python, SQLMap.
8. Basic Web Scraper
Objective: Design a web scraper to extract data from websites and understand how to handle scraping ethically.
Description: A web scraper collects data from websites. This project teaches web scraping techniques while adhering to ethical guidelines and respecting website terms of service.
Tools: Python, BeautifulSoup, Scrapy.
9. Phishing Email Simulator
Objective: Create a tool to simulate phishing emails for training and educational purposes.
Description: This tool generates simulated phishing emails to train users in recognizing phishing attempts, thus improving their ability to handle real phishing attacks.
Tools: Python, Email Libraries.
10. Traffic Analyzer
Objective: Develop a simple tool to analyze the types of traffic on a network and identify unusual patterns.
Description: A traffic analyzer monitors network traffic to differentiate between normal and abnormal activity, helping to detect potential security issues and monitor network health.
Tools: Python, Wireshark.
11. Packet Sniffer
Objective: Create a tool to capture and analyze network packets.
Description: This tool captures packets traveling across a network and allows for detailed analysis. It helps in understanding network protocols and identifying suspicious traffic.
Tools: Wireshark, Scapy.
12. HTTP Header Analyzer
Objective: Build a tool to analyze HTTP headers from web requests.
Description: This tool examines HTTP headers to find security-related information and vulnerabilities, such as outdated software or insecure configurations.
Tools: Python, Requests Library.
13. Basic Encryption/Decryption Tool
Objective: Develop a tool to encrypt and decrypt text using basic algorithms.
Description: This project helps people understand encryption and decryption methods by creating a simple tool for secure communication and demonstrating basic cryptographic techniques.
Tools: Python, Cryptography Library.
14. Simple Web Application Firewall (WAF)
Objective: Create a basic WAF to filter and monitor HTTP requests.
Description: A Web Application Firewall (WAF) helps protect web applications by filtering out malicious requests. This project involves building a basic WAF to understand its role in web security.
Tools: Python, Flask.
15. Social Engineering Toolkit
Objective: Develop a toolkit to simulate social engineering attacks.
Description: This toolkit helps in training users to recognize and respond to social engineering attacks, enhancing their awareness and defensive skills.
Tools: Python, Social Engineering Toolkit (SET).
16. Network Bandwidth Monitor
Objective: Build a tool to monitor and analyze network bandwidth usage.
Description: This tool tracks network bandwidth usage, providing insights into network performance and detecting unusual activities that may indicate security issues.
Tools: Python, SNMP Libraries.
17. Basic Malware Detector
Objective: Create a simple tool to detect known malware signatures.
Description: This project involves building a basic malware detector that searches for known malware patterns in files, aiding in identifying and preventing malware infections.
Tools: Python, YARA.
18. Vulnerability Assessment Tool
Objective: Develop a tool to assess common vulnerabilities in a system or application.
Description: This tool identifies common security vulnerabilities, such as misconfigurations or outdated software, helping to improve overall system security.
Tools: Python, OpenVAS.
19. Wi-Fi Network Scanner
Objective: Create a tool to scan and analyze Wi-Fi networks.
Description: This tool identifies nearby Wi-Fi networks, their signal strengths, and potential security issues, useful for network analysis and security assessments.
Tools: Python, Kismet.
20. Simple DNS Spoofing Tool
Objective: Build a tool to demonstrate DNS spoofing attacks.
Description: DNS spoofing involves redirecting DNS queries to malicious sites. This tool demonstrates DNS spoofing techniques and helps understand how to protect against such attacks.
Tools: Python, Scapy.
21. Email Header Analyzer
Objective: Develop a tool to analyze email headers for security insights.
Description: This tool inspects email headers to identify potential security issues, such as spoofed sender addresses or malicious attachments.
Tools: Python, Email Libraries.
22. Local Network Mapper
Objective: Create a tool to map devices on a local network.
Description: This tool scans a local network to discover connected devices and their IP addresses, aiding in network management and security assessments.
Tools: Python, Nmap.
23. Web Form Fuzzer
Objective: Build a tool to test web forms for input validation vulnerabilities.
Description: A web form fuzzer sends a variety of inputs to web forms to identify issues such as input validation flaws or error handling vulnerabilities.
Tools: Python, Burp Suite.
24. Basic Firewall Tester
Objective: Create a tool to test the effectiveness of firewall rules.
Description: This tool evaluates firewall rules by attempting to bypass them and identifying potential weaknesses in firewall configurations.
Tools: Python, Nmap.
25. Log Monitoring Tool
Objective: Develop a tool to monitor and analyze system logs for suspicious activities.
Description: This tool examines system logs to detect unusual patterns or potential security breaches, aiding in early threat detection.
Tools: Python, Logwatch.
26. SSH Brute Force Tester
Objective: Build a tool to test SSH login attempts using brute force.
Description: This project involves creating a tool that attempts multiple SSH login attempts to identify weak passwords and improve security measures.
Tools: Python, Hydra.
27. HTTP/HTTPS Traffic Analyzer
Objective: Create a tool to analyze HTTP and HTTPS traffic.
Description: This tool monitors and analyzes HTTP/HTTPS traffic to detect anomalies, secure communication, and potential attacks.
Tools: Python, Wireshark.
28. Basic IDS (Intrusion Detection System)
Objective: Develop a basic IDS to detect suspicious network activities.
Description: An IDS monitors network traffic for signs of intrusion or abnormal behavior, helping to detect potential attacks and secure the network.
Tools: Snort, Suricata.
29. Penetration Testing Report Generator
Objective: Create a tool to generate penetration testing reports.
Description: This tool compiles findings from penetration tests into a structured report, including discovered vulnerabilities and recommendations for fixes.
Tools: Python, ReportLab.
30. Simple SSL/TLS Checker
Objective: Build a tool to check SSL/TLS configurations for weaknesses.
Description: This tool evaluates SSL/TLS settings to ensure they meet security standards, helping protect against attacks on encrypted communications.
Tools: Python, OpenSSL.
31. Localhost Security Scanner
Objective: Create a scanner to assess the security of localhost services.
Description: This tool scans services running on localhost for common vulnerabilities and misconfigurations, enhancing local system security.
Tools: Python, Nmap.
32. Basic Web Crawler
Objective: Develop a simple web crawler to explore and extract data from websites.
Description: A web crawler navigates through web pages to collect data. This project helps us understand web navigation and data extraction techniques.
Tools: Python, BeautifulSoup.
33. Session Hijacking Demonstrator
Objective: Build a tool to demonstrate session hijacking techniques.
Description: This tool shows how attackers can hijack sessions and how to secure session management to prevent unauthorized access.
Tools: Python, Scapy.
34. FTP Vulnerability Scanner
Objective: Create a tool to scan FTP servers for security vulnerabilities.
Description: This tool checks FTP servers for common security issues, such as weak passwords or insecure configurations, to enhance FTP security.
Tools: Python, Nmap.
35. Basic HTTP Request Spoofer
Objective: Build a tool to spoof HTTP requests.
Description: This tool modifies and sends HTTP requests to test web applications for vulnerabilities related to request manipulation and header spoofing.
Tools: Python, Requests Library.
36. Simple Cookie Editor
Objective: Develop a tool to edit and analyze HTTP cookies.
Description: This tool allows users to modify HTTP cookies and observe the effects, helping understand cookie-based vulnerabilities and security.
Tools: Python, Browser Developer Tools.
37. Basic Directory Scanner
Objective: Create a tool to scan directories and files on a web server.
Description: This tool scans web servers for accessible directories and files, identifying potential security risks and improving web application security.
Tools: Python, DirBuster.
These projects are designed to help beginners gain practical experience in ethical hacking and cybersecurity. Each project includes specific tools to facilitate development and testing.
Essential Skills and Requirements for Starting Ethical Hacking Projects
Before you start with ethical hacking project ideas, you need to build a strong foundation in some key areas. Here’s a simple guide to what you need:
1. Understanding Computer Networks
What You Need:
- Know how network protocols work (like TCP/IP, HTTP, FTP).
- Understand basic network devices (routers, switches, firewalls).
- Be familiar with IP addresses and subnetting.
Why It Matters: Understanding how networks work helps you find weak spots and see how attacks can move through a network.
2. Knowledge of Operating Systems
What You Need:
- Experience with both Windows and Linux.
- Comfort with using command-line tools.
Why It Matters: Many hacking tools work best on specific operating systems. Knowing Linux is especially useful because it’s often used in security work.
3. Basics of Cybersecurity
What You Need:
- Understand common threats and vulnerabilities (like malware, phishing, SQL injection).
- Know basic security principles (like confidentiality, integrity, availability).
- Be familiar with encryption and hashing.
Why It Matters: Knowing these basics helps you spot and fix security issues more effectively.
4. Basic Programming Skills
What You Need:
- Know how to use at least one programming language (like Python or JavaScript).
- Be able to write simple scripts and automate tasks.
Why It Matters: Programming helps you create custom tools, automate tasks, and understand how software can be attacked.
5. Familiarity with Hacking Tools
What You Need:
- Know how to use common tools (like Nmap, Wireshark, Metasploit, and Burp Suite).
- Be able to use these tools for tasks like scanning and testing.
Why It Matters: These tools are essential for finding security weaknesses and assessing systems.
6. Understanding Legal and Ethical Guidelines
What You Need:
- Know the rules and laws about ethical hacking.
- Understand the importance of getting permission before testing systems.
Why It Matters: Following legal and ethical guidelines ensures your work is responsible and respectful of others.
7. Analytical and Problem-Solving Skills
What You Need:
- Be good at analyzing systems and finding weaknesses.
- Have strong problem-solving skills to address security issues.
Why It Matters: Ethical hacking often involves solving complex problems, so being able to think critically is key.
8. Willingness to Keep Learning
What You Need:
- Stay up to date on newest cybersecurity trends and dangers.
- Be open to learning new tools and techniques.
Why It Matters: Cybersecurity is always changing, so staying current is important to remain effective.
In summary, to start ethical hacking projects, you need to understand computer networks, operating systems, and basic cybersecurity concepts. Programming skills, knowledge of hacking tools, and an understanding of legal and ethical guidelines are also important. Good analytical skills and a willingness to keep learning will help you succeed.
Essential Tools and Tips for Ethical Hacking Projects
When starting with ethical hacking, using the right tools and following good practices is key. Here’s a straightforward guide to help you get started:
Essential Tools
- Nmap
- What It Does: Scans networks to find active devices, open ports, and services running on those ports.
- Why It’s Useful: It helps you understand what’s on a network and where potential vulnerabilities might be.
- Wireshark
- What It Does: Captures and analyzes network traffic.
- Why It’s Useful: It lets you see what’s happening on a network and spot any suspicious activity.
- Metasploit
- What It Does: Provides tools for finding and exploiting security weaknesses.
- Why It’s Useful: It allows you to analyze the efficiency of your security measures and identify potential threats.
- Burp Suite
- What It Does: Tests web applications for security issues.
- Why It’s Useful: It helps you find common web vulnerabilities, such as SQL injection or cross-site scripting (XSS).
- Nessus
- What It Does: Scans systems for known vulnerabilities.
- Why It’s Useful: Identifies weaknesses in your systems that need to be addressed.
- Aircrack-ng
- What It Does: Tests the security of wireless networks.
- Why It’s Useful: It helps you check and crack encryption on Wi-Fi networks to determine their security.
- Hydra
- What It Does: Cracks passwords through brute-force attacks.
- Why It’s Useful: It helps you test the strength of your passwords and authentication methods.
- John the Ripper
- What It Does: Cracks password hashes.
- Why It’s Useful: Useful for testing password security by cracking hashed passwords.
- OWASP ZAP (Zed Attack Proxy)
- What It Does: Tests web applications for security issues.
- Why It’s Useful: Helps you find and fix vulnerabilities in web apps through automated and manual testing.
- Kali Linux
- What It Does: A Linux distribution packed with security tools.
- Why It’s Useful: Provides a complete suite of tools for various security testing tasks.
Tips for Effective Ethical Hacking
- Get Permission
- Always make sure you have explicit permission before testing any system. Hacking without consent is illegal and unethical.
- Know Your Limits
- Clearly define what systems and areas you’re allowed to test. Stick to these boundaries to avoid any legal issues.
- Keep Detailed Records
- Document everything you do, including the tools you use and what you find. This information is crucial for reporting and fixing issues.
- Follow a Plan
- Use structured methods, such as the OWASP Testing Guide or NIST frameworks, to ensure that your testing covers all the bases.
- Stay Updated
- Cybersecurity is always changing. Keep up with the latest trends, tools, and threats to stay ahead.
- Practice Safely
- Use virtual machines and test environments to practice your skills. This way, you can experiment without risking real systems.
- Use a Mix of Tools
- Different tools offer different insights. Combining them can give you a more comprehensive view of your security.
- Understand the Rules
- Know the laws and ethical guidelines related to hacking. This ensures you’re conducting your work responsibly.
- Communicate Clearly
- When you find issues, explain them clearly and provide practical recommendations for fixing them.
- Keep Learning
- The field of ethical hacking is always evolving. To remain effective, you should continue to study and update your abilities.
By using these tools and following these tips, you’ll be well-equipped to handle ethical hacking projects responsibly and effectively.
Final Words
Getting into ethical hacking is both exciting and challenging. With the 35+ Best Ethical Hacking Project Ideas For Beginners In 2024, you have plenty of great projects to help you get started. Using the right tools and following the best practices can make a big difference in finding and fixing security issues and keeping systems and data safe from threats.
To succeed, you’ll need a good mix of technical skills, an understanding of legal and ethical rules, and a willingness to keep learning. By exploring these project ideas and using the tips we’ve discussed, you’ll build a strong foundation in cybersecurity. Stay curious, keep learning, and always be responsible in your work.
FAQs
Are there legal issues with ethical hacking?
Yes, ethical hacking must always be done with permission from the system owner. Testing or accessing systems without authorization is illegal and can lead to serious legal trouble. Always get explicit consent before you start.
What should I document during ethical hacking projects?
Document your process, including the tools and methods you use, any vulnerabilities you find, and how to fix them. This helps you create clear reports and keep a record of what you did.
Where can I find more resources for learning ethical hacking?
You can find more resources through online courses, cybersecurity forums, blogs, books, and certifications. Joining the cybersecurity community and practicing in virtual labs will also help you learn and grow.


